Application Onboarding
For enterprises who need to onboard applications to their Identity Governance and Administration (IGA) system, the Application Onboarding Service enables the organisation to enforce appropriate access to sensitive information within those applications.
Unlike traditional approaches, our service will onboard applications to your IGA system and manage its integration’s lifecycle in a secure, systematic, and predictable manner.
Integration approach
We build integrations between an Identity Governance and Administration (IGA) system and any application. To increase the speed of adding business value we use a 3-step integration approach.
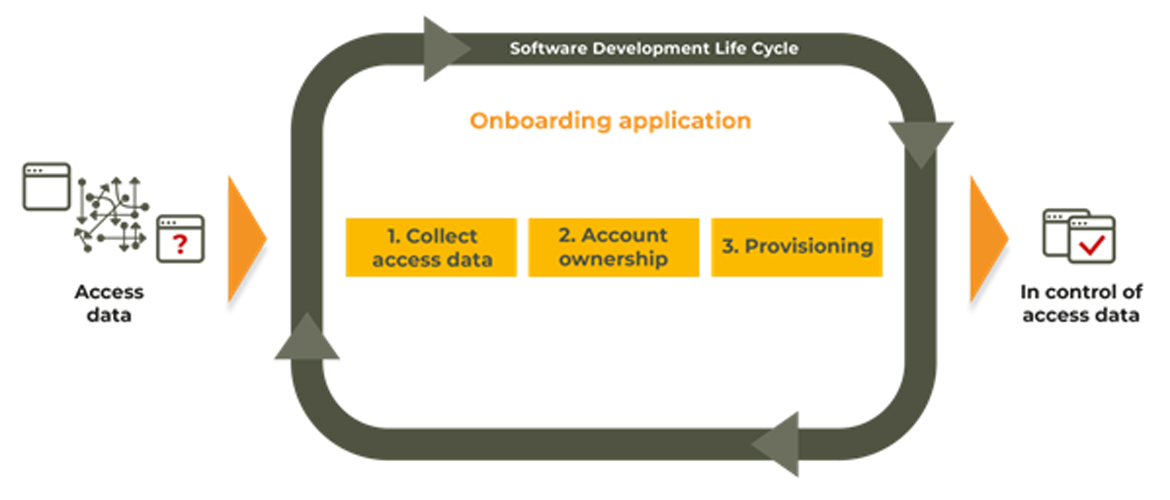
Collect access data
Provides a centralised insight into the current state of the access data within the application being onboarded. This will give the application owner insight into what accounts are present and what permissions are granted to these accounts.
Account ownership
Verify if identities are supposed to have access to the application being onboarded. This will give the Application Owner insights into the actual state. The Application Owner can then shape the desired state by reviewing the collected access data and take actions based on the review.
Provisioning
Enforce appropriate access to the application by adding, updating and deleting related access data (i.e., accounts and permissions). This will also give the Application Owner insights into what access data has been added, updated and deleted.
A broad selection of applications
We can onboard a broad selection of applications including applications using non-standard protocols and/or integration approaches.
A wide variety of IGA systems
We can deliver the onboarding service using a wide variety of Identity Governance & Administration (IGA) Systems. Some examples of our partners are: SailPoint, Omada, and Microsoft.
Out-of-the-box standardisation
We can enable your organisation to leverage the benefits of a standardised integration by combining the onboarding service with products we provide such as the SCIM Gateway.
Well-documented
Our products are shipped with outstanding documentation that takes you step by step through the installation and configuration process.
Great customer support
Do you have some specific use cases that require extra attention? No problem, our technical support experts are more than happy to help with any questions and challenges you might have.
Can we help you?
Are you looking for a service provider that is capable of onboarding any type of application to your IGA system? Is clear communication and delivery quality important to you?
“My experiences with Red5 summarised: a lot of knowledge, a lot of flexibility and a lot of enthusiasm. During the project, we also received sufficient attention from account management and we continuously thought about how Red5 could help us further”
Mark B – Head of Cyber Security, Global Financial Services Company

