Compliance
The security landscape is constantly evolving, bringing with it new legislative and regulatory frameworks or guidelines to comply with. Red5 has either helped to make them or knows them inside and out. Our global business helps organisations achieve the right level of assurance to meet both government and industry compliance standards – locally or when your business needs to go global.
Why Red5?
Compliance experts
Our experts have experience working with every major compliance framework, including GDPR, NIST, HITRUST, UNECE and more.
Security first
Go beyond “checking the box” to ensure the security of your most critical assets.
Forward looking
Stay prepared as compliance mandates evolve and gain a business advantage over the competition.
Our Compliance Service
From security testing to strategic advisory, Red5 is here to solve your most pressing security challenges. Our experts leverage years of industry expertise to give your teams critical insight and guidance on a variety of security areas. Identify vulnerabilities targeting your organisation, uncover security gaps, meet and maintain regulatory compliance, and more.
ISO
Undertake an external audit and meet all compliance criteria with the International Organisation for Standardisation (ISO) standards, including ISO 27001 and ISO/IEC 17025:2015. Red5 consultants have achieved ISO 27001 certification and are ideally placed to help implement the standard as well as achieve certification.
The National Institute for Standards and Technology Cyber Security Framework
NIST CSF provides guidance for carrying out risk assessments and describes the interrelationships between the various components of the organisational risk management process. 80% of Red5 clients request they be assessed using the NIST CSF.
Common Criteria (CC)
CC is an international standard for computer security certification. Where a product category has an international CC PP available, we are able to support you in evaluating CC against the equivalent CPA Security Characteristic (SC).
CESG Tailored Assurance Service (CTAS)
CC is an international standard for computer security certification. Where a product category has an international CC PP available, we are able to support you in evaluating CC against the equivalent CPA Security Characteristic (SC).
Cyber Essentials
Suppliers bidding for contracts with the UK Government can demonstrate their ability to securely handle sensitive and personal information by certifying against the Cyber Essentials scheme. This service is also suitable for organisations of any size, in any sector.
G Cloud
Ensure you are compliant with the UK Government Cloud (G-Cloud) program to sell cloud hosting, software, and support services on the Digital Marketplace.
IT Heath Check Service (CHECK)
The NCSC IT Health CHECK (ITHC) or CHECK scheme was developed by the UK Government’s information assurance division. We possess CHECK Green status (the highest level of assurance) and can implement an IT Health Check in less than a month.
Commercial Product Assurance
The CPA scheme is designed to provide additional assurance to HMG when choosing commercial security products. The UK scheme is administered by NCSC, the Government’s National Technical Authority for Information Assurance.
Cyber Security Maturity Model
We can assist your organisation in understanding and complying with Federal Acquisition Regulation (FAR) and Defence Federal Acquisition Regulation (DFAR) and prepare for CMMC. Red5 consultants stay current with both the DoD Office of the Under Secretary of Defence for Acquisition & Sustainment and CMMC Accreditation Body updates.
Civil Aviation Authority (CAA) ASSURE
To achieve ASSURE accreditation, Red5 Consultants are subject to a rigorous and continuous accreditation process under the ASSURE framework. We have ASSURE Cyber Professionals accredited to conduct audits in all of the following three specialisms: Cyber Audit & Risk Management, Technical Cyber Security, and Industrial Control Systems.
Data Privacy
Ensure compliance with data privacy regulations and embed privacy-driven design principles into your business operations.
Government & Regulations
Navigate the complexities of government security requirements to gain new business and maintain existing contracts.
Payments
Ensure your system components are PCI-DSS compliant.
ISO 27001 Audit & Implemntation
For those new to ISO 27001, the audit process can indeed appear daunting. It’s a substantial, complex task that even seasoned professionals may find challenging. However, like many challenges, adequate preparation can help alleviate concerns. As you gain a better understanding of the process, it becomes less intimidating.
If your organistion is pursuing certification with the assistance of a consultancy like Red5, you can expect a pre-certification audit and assurance exercise to be conducted before your scheduled certification audit. This preliminary step aims to assess whether your Information Security Management System (ISMS) aligns with all the necessary criteria.
Think of this as a pre-certification “dry run” or “rehearsal” audit. It serves several purposes:
Issue Identification:
It helps identify potential issues that can be addressed before the actual certification audit.
Familiarisation:
It allows your organisation’s members to become familiar with the audit process, reducing anxiety on the actual certification day.
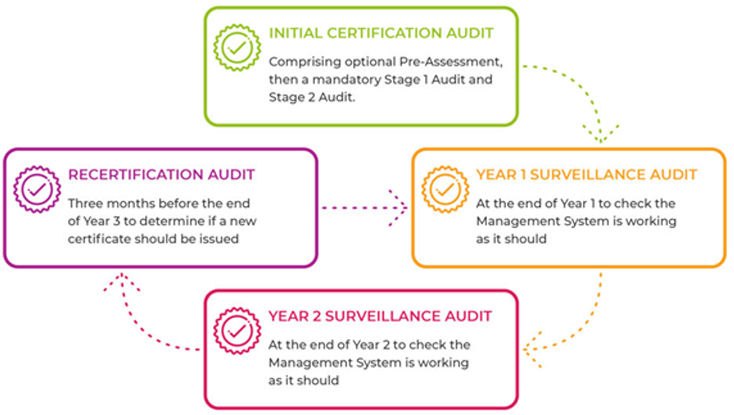
The certification audit, typically conducted by an independent third-party certification body (CB) selected by your organisation, consists of two stages: ‘Stage 1’ and ‘Stage 2’ audits.
Stage 1 Audit:
The Stage 1 audit is often referred to as a ‘documentation review’ audit. During this stage, the assigned auditor examines your documentation process to ensure that the ISMS aligns with both ISO 27001 requirements and your organisation’s defined criteria. Your organisation must provide evidence of various aspects of the ISMS, such as policies, procedures, and processes. The extent of information required depends on the certification body’s requirements.
This stage is more of an ‘investigation’ or ‘exploration’ audit. The auditor conducts a high-level review to understand your ISMS and assess the design of security controls. The length of this assessment varies based on your organisation’s size and industry. After the Stage 1 audit, the auditor will highlight any nonconformities and suggest improvements. Nonconformities are typically categorised as minor or major, with major issues needing immediate attention.
Stage 2 Audit:
If your organisation successfully clears the Stage 1 audit, the auditor will proceed to the Stage 2 audit, often referred to as the ‘certification audit.’ This stage involves a comprehensive, on-site assessment to confirm that your ISMS complies with ISO 27001.
During this assessment, the auditor reviews activities and procedures in more depth, ensuring they align with ISO 27001 standards. The auditor also conducts meetings and interviews with key staff to validate compliance. Evidence of adherence to documentation reviewed in Stage 1 is sought, including internal audits and management reviews.
If your organisation passes this stage, the auditor will recommend it for certification, subject to an internal review by the certification body. Once this process is completed, your organisation will receive an ISO 27001 certification, valid for three years.
To maintain your certification, annual surveillance activities and a full re-assessment every fourth year are required. Here are some measures for maintaining your certification:
- Keep your certification body informed of any changes affecting certification scope.
- Ensure key technical staff maintain their competence through training and sector event participation.
- Stay updated on regulatory changes in your sector.
- Subscribe to updates from certification authorities and technical publications.
- Notify relevant parties in advance of any premises relocation.
- Implement an internal audit regime.
- Maintain effective document control.
- Retain quality and technical records.
- Adopt the PDCA (Plan-Do-Check-Act) model for continuous improvement of cybersecurity processes and activities.
By following these measures, organisations can successfully maintain their ISO 27001 certification and ensure ongoing information security governance.
For more information on how Red5 can support your organisation, get in touch with our team for a confidential conversation.

